Speaker: Wade Ellery, VP of Solutions Architects, Radiant Logic
Date: Wednesday, June 22, 2022
Location: Denver, CO
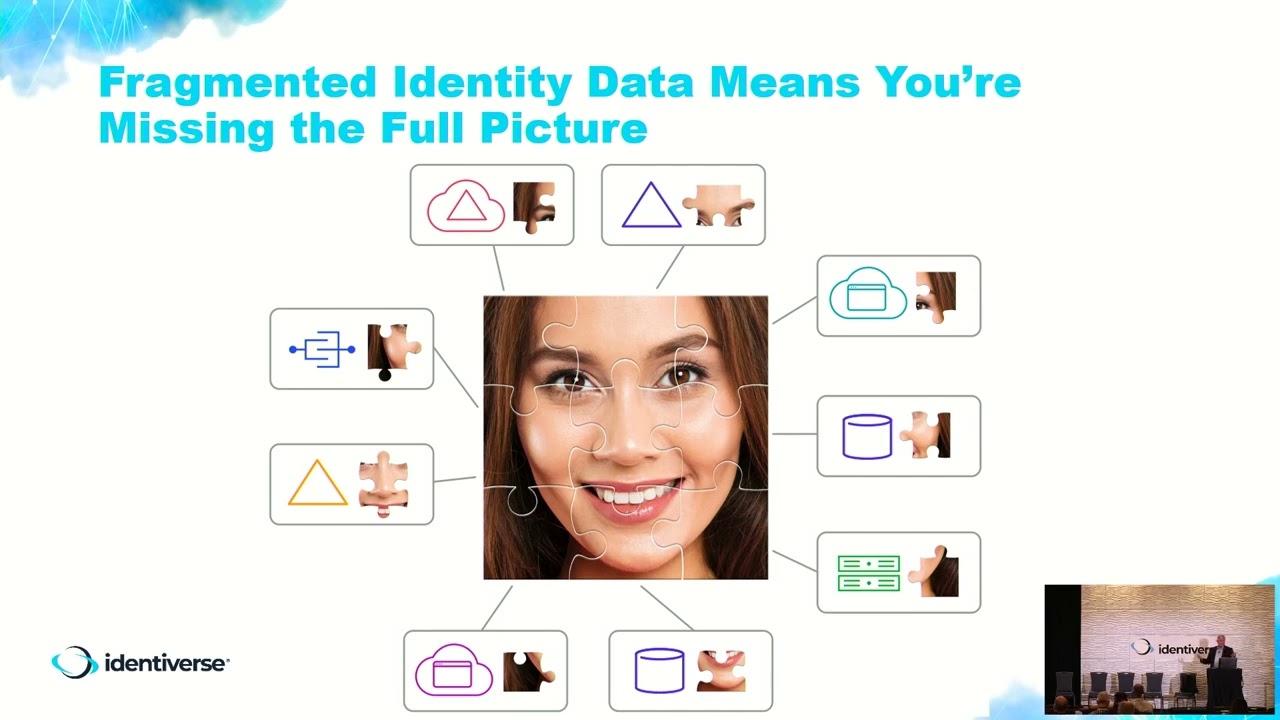
Description: Zero Trust—who isn’t talking about it?! If you’re not, you should be. According to a recent survey of technology leaders, zero trust is the highest prioritized investment in the next year. This modern approach to security and access is critically dependent on accurate, complete, and up-to-date identity data for your users across the enterprise. However, as IT sprawl accelerates and larger attack surfaces emerge, identity information is now spread across legacy, hybrid, and multi-cloud systems. How can you ensure the least privilege access without putting an excessive burden on your organization’s resources and end-users? It can be overwhelming and paralyzing.
What if you could start to gain visibility and control over all your sources of identity today? Start to build a 360-degree view of identity regardless of the source of truth. Create an Identity Data Fabric that incorporates all the components of Zero Trust data from endpoints to user profiles. Then feed these correlated and normalized sources of identity truth to each component of the Zero Trust architecture from Policy Based Access to Governance to Risk Management and Network Segmentation. And, do all this while leveraging your existing investments in ICAM, avoiding disruption of business processes, and smooth the journey to Zero Trust in days.
In this masterclass, VP of Solutions Architects Wade Ellery will explain how to unlock identity data so you can close security gaps and lay your Zero Trust foundation. With real-life lessons based on deployments at the Fortune 500, and insights gleaned from the NIST labs, Wade will show why Zero Trust doesn’t have to be that hard, and why it all starts with your identity data.
Attendees will learn:
● How to identify the first (and most foundational) steps to take on the Zero Trust journey
● Knocking out some of the typical stumbling blocks for delivering enhanced security frameworks ● How to get the fabled “single source of identity truth” once and for all
● How to deliver each application and platform exactly the identity data it needs, in the subset of users, attributes, format, structure, and protocol it requires
● Some quick tips for combating loss of control over identity
● Best practices for the management, use, and protection of that most critical resource— identity data