Speaker: Brian Campbell, Distinguished Engineer, Ping Identity
Date: Thursday, June 23, 2022
Location: Denver, CO
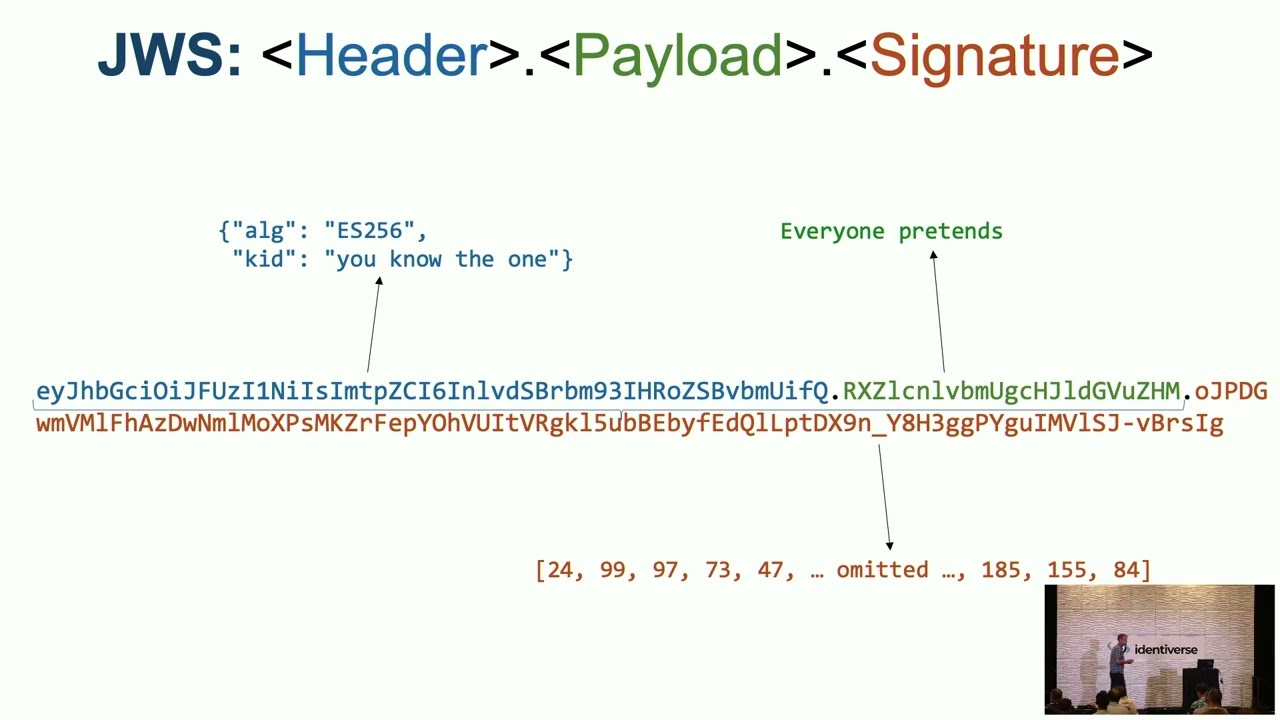
Description: JWT is an IETF standard security token format that, due to perceived simplicity and widespread library availability, has been extremely popular in recent years. Despite that popularity (or maybe, in part, because of it), JWT has been heavily derided by reputable people in information security (“horrible standard”, “RFC was made by monkeys”, “Internet’s worst cryptography standard”, “JWT is a disaster … amazing how bad it is”, “simplistic, complicated, and unsafe all at the same time”, and “almost impossible to build a secure JWT library” …give just a taste of the sentiment).
The criticism has been substantiated and amplified by a steady stream of public vulnerabilities in libraries and deployments. Indeed there have been serious and legitimate security problems with JWT and many of them can be attributed directly to fundamental flaws in the specification itself that allowed, or even encouraged, such implementation mistakes. But is JWT irredeemably flawed? This session will endeavor to take a hard look at that very question (complete with the presenter’s own sense of inadequacy and fear of culpability in JWT’s flaws) with a review/overview of JWT fundamentals and a pragmatic look at each of the most common and/or biting criticisms and associated real-world vulnerabilities.