Speakers: Pieter Kasselman, Program Manager, Microsoft
Date: Friday, June 24, 2022
Location: Denver, CO
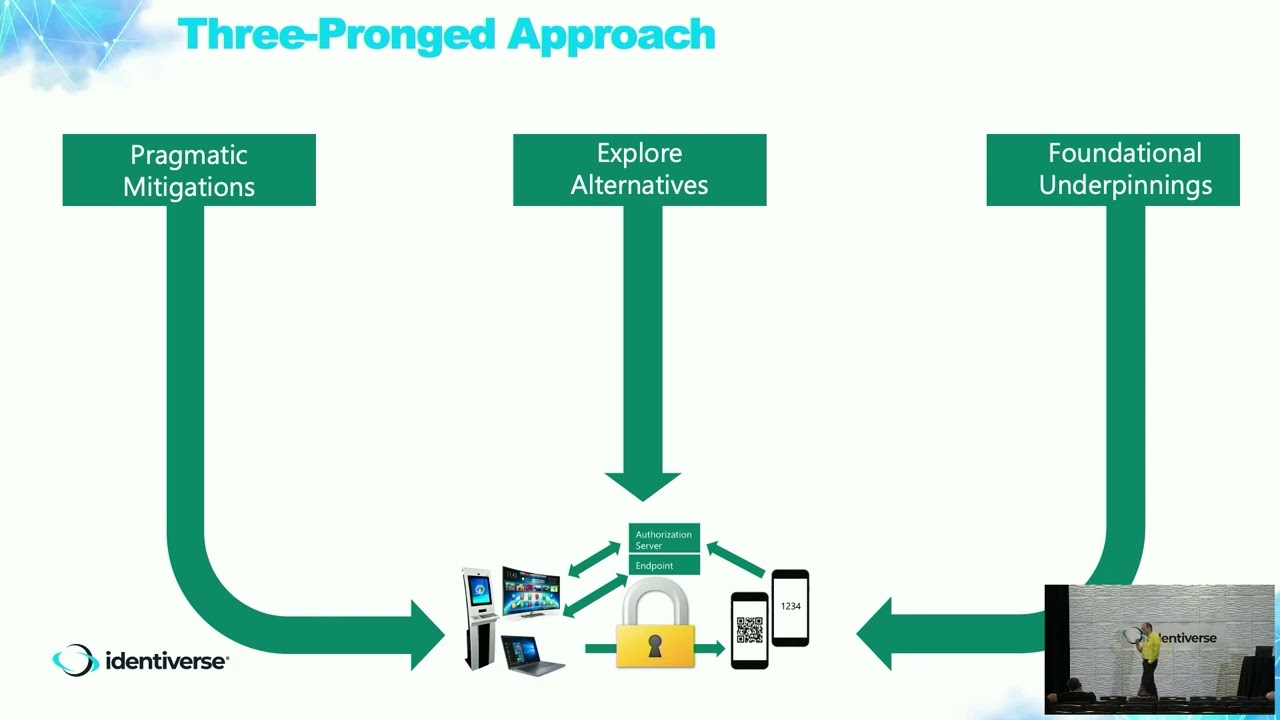
Description: Cross device flows allows users to initiate an action on one device and then authenticate or authorize that action on a trusted device like a mobile phone. An example of this includes authorizing a smart TV to access streaming content, or authenticating to a service by scanning a QR code with a mobile phone and completing the authentication on the mobile phone. This process of authorizing an action on a separate (but trusted) device from the one on which an action is initiated is an increasingly common flow, whether used for devices with limited input capabilities, multi-factor authentication or credential presentation. A number of standards have adopted this pattern including Device Authorization Grant (formerly Device Code Flow), Client Initiated Backchannel Authentication (CIBA) and Self Issued OpenID Provider (SIOP). These flows solve important business problems, but is vulnerable to attacks where the user is tricked into granting consent to an attacker. Defending against these “illicit consent grant” attacks requires an in-depth defense strategy. This session will discuss mitigations needed to maintain trust in cross device flows based on an analysis of known exploits and the protocols involved.